�m���ɡnFreeradius�POpenSSL���� �m���ɡnFreeradius�POpenSSL���� |       |
�̪�b����Freeradius�W���U��EAP�{�Ҿ���C
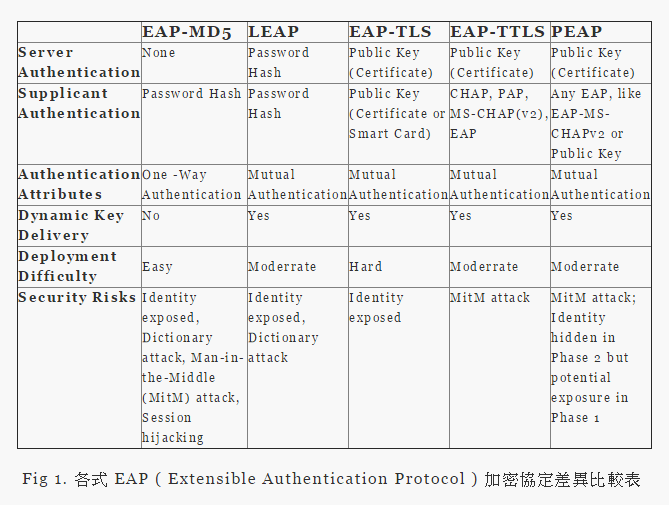
Freeradius�W�䴩�FEAP-MD5�BLEAP�BEAP-TLS�BEAP-TTLS��EAP-PEAP���h��EAP�`���{�Ҩ�w�A
���F�w�]��EAP-MD5�֤F�ۤ��{�Ҩ�(Mutual Authentication)�A�䥦4�ؾ���䴩�ۤ��{�ҡC
��EAP-TLS�BEAP-TTLS��EAP-PEAP�o�T�ؾ���A��ݭn���ҨӶi���ƥ[�K�ǿ����ҡC
����b�w��FreeRadius��Ubuntu�W�A�O�p�ͳo�Ǿ��ҩO�H
���bUbuntu 14.04�W�w�˦nFreeradius��A�u�n�U�F freeradius -X ���O�A
�t�δN�|�� /etc/freeradius/certs �ؿ��U�A�z�Lbootstrap�ɮפ���script�ӫإ߹w�]��snake oil���ҨѨϥΪ̶i����աC
�Y�ڭ̷Q�n�إߦۤv�����ҡA�i�ѦҤU�ϤF�Ѿ��ҥ@�ɤ����������p�A�z�L���ت�OpenSSL�Ӷi��C
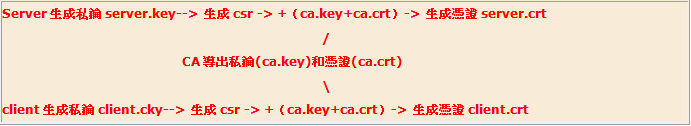
�����S���o垷client�Mserver���ӽЬy�{�O�����ۦP���I�H
�ѦҸ��
SSL�����Oopenssl���w装
Production Certificates
OpenSSL - ���_�P���Ҫ��z
�ϥ� freeRadius �]�m 802.1X �{������(�T)EAP-TLS�g

♥���l�ѱC������A�Цh���ӡ�
If you don't like something, change it.
If you can't change it, change your attitude.
Don't complain!
|